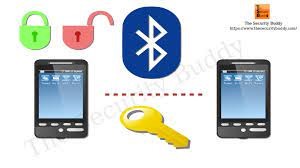
Bluebugging is a type of Bluetooth attack that is often caused by a lack of awareness. It was developed after the advent of bluejacking and bluesnarfing. Similar to bluesnarfing, Bluebugging accesses and uses all the features of phone without the permission of user ,but it is limited by the transmitting power of class 2 Bluetooth radios, normally range at 10–15 meters. However, the operational range can be enhanced with the use of a directional antenna.
Bluebugging was developed by the German researcher Martin Herfurt in 2004, a year after the onset of bluejacking Initially it was a threat against laptops with Bluetooth capability but later targeted mobile phones and PDAs.
Bluebugging forces a targeted phone to compromise with its security, this to create a backdoor attack before returning control of the phone to its owner. Once control of a phone has been set, it is used to call back the hacker who is then able to listen even the conversations, hence it’s named as “bugging”. The Bluebug program also has the capability to create a call forwarding application whereby the hacker receives calls intended for the targeted phone.
A further development of Bluebugging has allowed the control of target phones through Bluetooth phone headsets, It achieves this by pretending to be the headset and thereby “tricking” the phone into obeying call commands. Not only a hacker can receive calls but also intended for the targeted phone, he can send messages, read phonebooks, and examine calendars too.
Generally, smartphones have their Bluetooth settings on discovery mode as it is a default setting, making it easy for hackers to access the phones when they are within 10 metres from the device. cybersecurity experts noted that Even the most secure smartphones like iPhones are also vulnerable to such attacks. Any app with access to Bluetooth can record users’ conversations with Siri and audio from the iOS keyboard dictation feature when using Air Pods or Beats headsets, a hacker can gain unauthorised access to these apps and devices and control them as per their will.
Difference between Bluejacking and Bluesnarfing:
- Bluejacking is the least harmful type of Bluetooth attack and involves sending unwanted messages over Bluetooth. If you have an discoverable Bluetooth connection, someone nearby you can use your Bluetooth to send messages that you don’t want. Though Bluejacking doesn’t install any app on your device or take control, it’s mostly harmless. It can be annoying and could be hurtful if the attacker sends inappropriate content, but it won’t cause any technical or monetary damage. Bluesnarfing and Bluebugging are a more serious threat.
- While Bluejacking presents unwanted content from the user, Bluesnarfing can take content from the victim. These attacks capture Bluetooth connections to steal passwords, images, contacts or other data from your phone or laptops.
- Bluesnarfing attacks cannot be easy to detect, too. While Bluejacking is immediately evident, you may not notice that someone is stealing your data from Bluetooth at first.
If you see any Bluetooth activity on your device that you are not initiating, then it could be a sign of Bluesnarfing.
How does it Works

- Bluebugging attacks work by using Bluetooth-enabled devices.
- The device’s Bluetooth must be in a pairing mode, which is the default setting on most devices.
- The hacker will now try to pair with the device via Bluetooth. Once a bluetooth connection is paired, hackers can use brute force attacks to bypass authentication.
- Hacker can then install a malware in the compromised device to gain unauthorised access to it.
- Bluebugging can occur whenever a Bluetooth enabled gazzet is within a 10-metre radius of the hacker.
Which devices are more susceptible to such attacks?
- Any Bluetooth-enabled device can be bluebugged.
- Wireless earbuds are more susceptible to such hacks. Apps that allows users to connect to their TWS (True Wireless Stereo) devices or earbuds can record conversations.
- Once the device is hacked, the hacker can make and listen to calls, read and send messages, and modify or steal your contacts.
Prevention Techniques:
- Turnoff the Bluetooth and disconnect the paired Bluetooth devices whenever not in use,
- Update the device’s system software to the latest version,
- Minimize the use of public Wi-Fi
- Using VPN for an additional security measure.
Read more on TechRuled



Pingback: What Is CHATGPT & How Does It Works? - Tech Ruled